Zero Trust Architecture
ConceptAbout
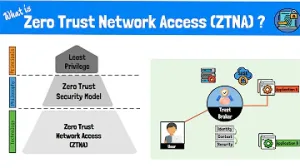
Zero Trust Architecture (ZTA) is a security framework that assumes all users and devices are untrusted, enhancing security by eliminating implicit trust within an organization's network. It requires continuous authentication, authorization, and validation of all entities before granting access to resources. This approach is crucial in modern digital environments, where threats can arise both inside and outside the network. ZTA is designed to protect against sophisticated attacks by ensuring that access is granted based on real-time risk assessments and least privilege access principles. Key principles of ZTA include default deny, risk-based verification, and comprehensive security monitoring. It involves identity verification, device compliance checks, and policy-based access controls. ZTA is particularly effective in cloud-based and remote work environments, where traditional perimeter security models are insufficient. Implementations like Zero Trust Network Access (ZTNA) and Zero Trust Application Access (ZTAA) further enhance security by limiting network and application access until verification is complete.