Implement Zero Trust Architecture
ConceptAbout
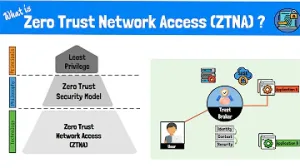
Implementing a Zero Trust Architecture (ZTA) is a comprehensive approach to security that requires continuous authentication and authorization for all access requests. This model assumes that no user or device should be trusted by default, regardless of whether they are inside or outside the network perimeter. By applying the principle of "never trust, always verify," ZTA significantly reduces the risk of unauthorized access and data breaches. Key components include identity and access management, micro-segmentation, and multi-factor authentication, ensuring that access is granted based on real-time risk assessments. ZTA involves several critical steps, including defining the protect surface, architecting a Zero Trust network, deploying Secure Access Service Edge (SASE), enforcing micro-segmentation, and applying the principle of least privilege. Continuous monitoring and dynamic policy adjustments are essential to adapt to evolving threats. By integrating these components, organizations can create a robust security framework that minimizes the impact of potential breaches and ensures a secure digital environment. This approach is particularly beneficial for modern infrastructures with diverse network environments and remote work setups.