

Best Habits to Prevent Ransomware and Malware Attacks
Regular Software Updates
Cybersecurity practicePatches vulnerabilities that could be exploited by malware and ransomware.

0 votes
Comprehensive Cybersecurity Training
ConceptEducates users on identifying and preventing threats, enhancing overall security posture.

0 votes
Email Security Measures
ConceptPrevents phishing and malicious attachments from entering the system.

0 votes
Multi-Factor Authentication
ConceptAdds an extra layer of security to prevent unauthorized access.

0 votes
Firewall Configuration
ConceptBlocks suspicious incoming traffic, protecting against external threats.

0 votes
Endpoint Hardening
ConceptSecures devices by limiting access and functionality, reducing vulnerabilities.

0 votes
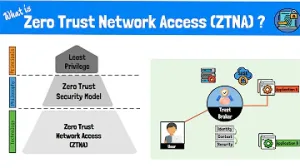
Least Privilege Access
ConceptRestricts user access to necessary resources, reducing potential attack vectors.

0 votes
Regular Offline Backups
ConceptEnsures data recovery in case of an attack by maintaining backups inaccessible to attackers.

0 votes
Network Segmentation
ConceptLimits the spread of malware by isolating network segments.
0 votes
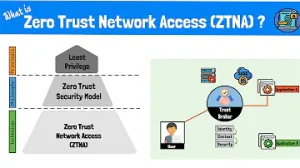
Implement Zero Trust Architecture
ConceptRequires authentication and authorization for all access, reducing the risk of unauthorized entry.
0 votes
Do you miss any participant in this ranking?
Add it yourself
Hey, your search results and suggestions will show up right here!
Hey, your search results and suggestions will show up right here!