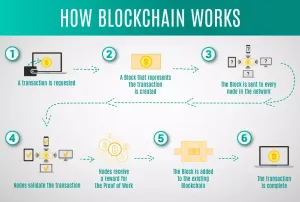
Main Trends in Cybersecurity for the Coming Years
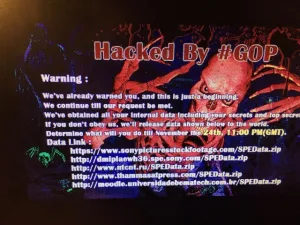
Supply Chain Attacks
Cybersecurity conceptAttackers target third-party vendors to compromise multiple organizations at once.

0 votes
Quantum Computing Threats
ConceptQuantum computing poses a threat to current encryption methods, necessitating quantum-resistant cryptography.

0 votes
AI-Powered Cyber-Attacks
TechnologyAI enhances the sophistication and elusiveness of cyber-attacks, making them harder to detect.

0 votes
State-Sponsored Cyber Warfare
ConceptNation-states engage in cyber warfare for espionage and geopolitical influence.

0 votes
Generative AI (Gen-AI) in Cybersecurity
ConceptGen-AI predicts threats with unprecedented accuracy and automates security systems.

0 votes
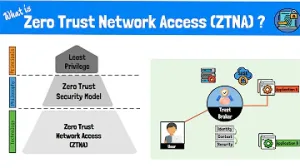
Zero Trust Architectures
ConceptZero trust models ensure continuous verification of user and device identities, enhancing security.

0 votes
Cloud Vulnerabilities
ConceptCloud environments are increasingly targeted due to their complexity and expanding use.

0 votes
5G and IoT Security Challenges
ConceptThe rollout of 5G and IoT devices expands the attack surface for cyber threats.
0 votes
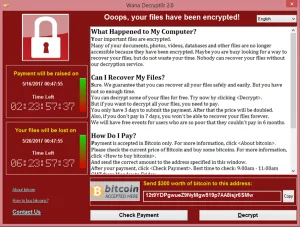
Ransomware-as-a-Service (RaaS) Evolution
ConceptRaaS makes it easier for attackers to execute ransomware attacks with minimal skill.

0 votes
Social Engineering via Deepfakes
Cybersecurity conceptDeepfakes enable sophisticated social engineering attacks, such as impersonation and identity theft.

0 votes
Do you miss any participant in this ranking?
Add it yourself
Hey, your search results and suggestions will show up right here!
Hey, your search results and suggestions will show up right here!