Top Cybersecurity Innovations for 2025
Biometric Encryption
ConceptBiometric encryption enhances authentication by converting unique physical traits into encrypted keys, reducing identity theft risks.

0 votes
AI-Driven Cybersecurity
ConceptAI enhances threat detection and response by analyzing vast amounts of data in real-time, enabling predictive analytics and automated incident responses.

0 votes
Behavioral Biometrics
Technology conceptBehavioral biometrics uses machine learning to analyze user behavior, detecting anomalies that could indicate unauthorized access.

0 votes
Secure-by-Design Principles
Security approachEmbedding security into product development from the outset reduces vulnerabilities and enhances resilience against cyber threats.

0 votes
Cloud Security Enhancements
Security strategyCloud security focuses on improving visibility, control, and data protection across multi-cloud environments through CSPM and SOAR systems.

0 votes
Quantum Computing and Post-Quantum Cryptography
ConceptQuantum computing poses a future threat to encryption, prompting the development of quantum-resistant algorithms to future-proof data security.

0 votes
Automated Patch Management
ConceptAutomating patch updates reduces vulnerabilities by quickly addressing software weaknesses, minimizing manual errors and breach risks.

0 votes
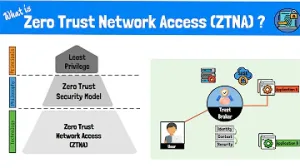
Zero Trust Architecture
ConceptZero Trust assumes no entity is trusted by default, emphasizing continuous verification and access controls to prevent unauthorized access.

0 votes
SOC Automation & Orchestration
Security strategySOC automation streamlines security operations by automating routine tasks, allowing human analysts to focus on complex threats.

0 votes
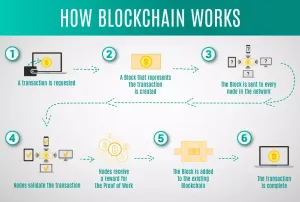
Blockchain Technology
Technology conceptBlockchain provides tamper-proof data storage and decentralized security solutions, reducing vulnerabilities by eliminating central points of failure.

0 votes
Do you miss any participant in this ranking?
Add it yourself
Hey, your search results and suggestions will show up right here!
Hey, your search results and suggestions will show up right here!