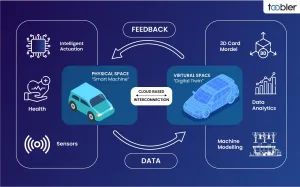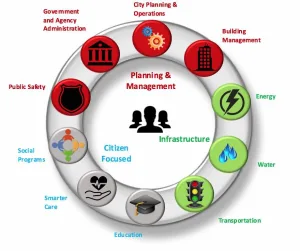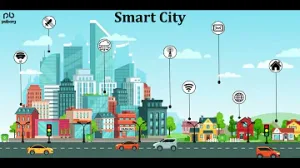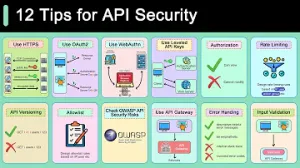

Main Security Risks in the Internet of Things
Insecure Ecosystem Interfaces
Security vulnerabilityPoorly secured APIs and interfaces can allow unauthorized access.

0 votes
IoT Botnets
Cyber threatCompromised devices can be used for DDoS attacks, overwhelming network traffic.

0 votes
Weak, Guessable, or Hardcoded Passwords
Security vulnerabilityMany IoT devices use default or hardcoded passwords, making them easy targets for hackers.

0 votes
Shadow IoT
Security riskUnauthorized IoT devices on networks can introduce unseen security risks.

0 votes
Unencrypted Data Transmissions
Security vulnerabilityUnencrypted data can be intercepted, exposing sensitive information.

0 votes
Absence of Device Management
Security riskLack of effective management makes it difficult to monitor and secure devices.

0 votes
Insecure Network Services
Security vulnerabilityUnencrypted communication protocols and outdated software expose IoT devices to attacks.

0 votes
Lack of Physical Hardening
Security riskDevices are often exposed and lack physical security measures.

0 votes
Insecure Default Settings
Security vulnerabilityDefault settings often include insecure configurations that are not changed.

0 votes
Lack of Secure Update Mechanism
Security vulnerabilityOutdated firmware and software leave devices vulnerable to exploits.

0 votes
Do you miss any participant in this ranking?
Add it yourself
Hey, your search results and suggestions will show up right here!
Hey, your search results and suggestions will show up right here!